A paper by two Belgian researchers has cast more light on the vulnerabilities discovered in the Wi-Fi Protected Access II (WPA2) implementations on most, if not all, wireless networking devices that use the protocol. Dubbed "KRACK" (Key Reinstallation AttaCK), the attack "abuses design or implementation flaws in cryptographic protocols to reinstall an already-in-use key," wrote Mathy Vanhoef and Frank Piessens of the Katholieke Universiteit Leuven (KU Leuven) in the paper, released today.
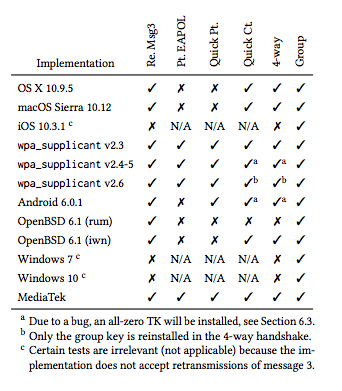
The report came after wide disclosure of the problems, as Ars reported Sunday night. The research is built upon previous explorations of weaknesses in WPA2's component protocols, and some of the attacks mentioned in the paper were previously acknowledged to be theoretically possible. However, the authors have turned these vulnerabilities into proof-of-concept code, "and found that every Wi-Fi device is vulnerable to some variant of our attacks. Notably, our attack is exceptionally devastating against Android 6.0: it forces the client into using a predictable all-zero encryption key."
While Windows and iOS devices are immune to one flavor of the attack, they are susceptible to others. And all major operating systems are vulnerable to at least one form of the KRACK attack. And in an addendum posted today, the researchers noted that things are worse than they appeared at the time the paper was written:
Although this paper is made public now, it was already submitted for review on 19 May 2017. After this, only minor changes were made. As a result, the findings in the paper are already several months old. In the meantime, we have found easier techniques to carry out our key reinstallation attack against the 4-way handshake. With our novel attack technique, it is now trivial to exploit implementations that only accept encrypted retransmissions of message 3 of the 4-way handshake. In particular this means that attacking macOS and OpenBSD is significantly easier than discussed in the paper.
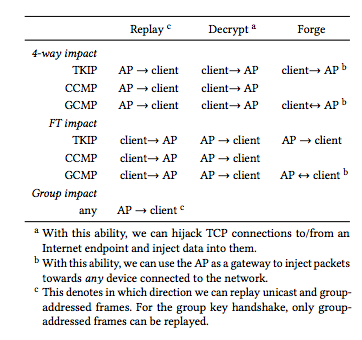
Wi-Fi networks typically use shared keys (usually based on AES encryption) to protect network traffic. That key is shared via a collection of cryptographic "handshakes" that verify the identity of network clients. The attack style documented by Vanhoef and Piessens targets those cryptographic handshakes: the four-way handshake used to initially pass a shared key to the client or the PeerKey Handshake used in peer-to-peer network connections; the group key refresh handshake used by the network to change the key when a client leaves the network; and the Fast Basic Service Set (BSS) Transition (FT) handshake used to allow clients to roam around a network with multiple access points.




 Loading comments...
Loading comments...
